Penetration Testing Methods (In-Depth info)
BSM Penetration Testing: Secure Your Network, Website, and IT Systems
A penetration test (pentest) is a simulated cyberattack on your network, website, or IT systems, conducted by ethical hackers with your explicit consent. The goal is to identify security vulnerabilities before malicious actors can exploit them. Pentesting is essential for organizations handling sensitive data and is often required to comply with standards like ISO 27001 and NEN 7510.
Clients may also require a Third-Party Memorandum (TPM) to demonstrate that their security measures have been independently verified.
What Does a Pentest Involve?
Our ethical hackers attempt to breach your systems using methods similar to those employed by real attackers. This process uncovers potential security risks and vulnerabilities within your organization. Often, it reveals that security measures are not as robust as initially thought. BSM provides detailed reports and recommendations to address identified issues.
When Is a Pentest Advisable?
Consider scheduling a pentest in the following situations:
If your systems have never been tested or haven’t been tested recently.
During the acceptance phase of a new system or application.
After significant changes to critical systems or applications.
As a periodic check to test existing systems against new attack techniques.
To verify the work of technical administrators or software developers, especially when outsourced.
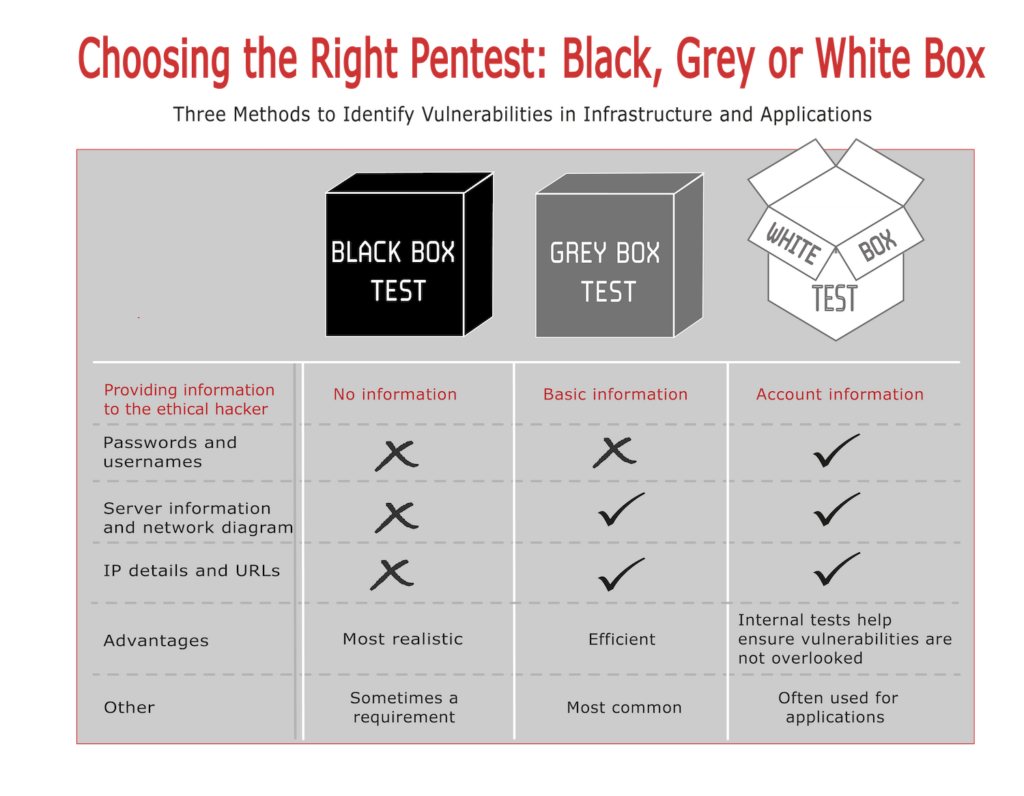
Types of Pentests
BSM offers three types of penetration tests, each varying in the amount of information provided to the tester:
1. Black box pentest
2. Grey box pentest
3. White box pentest
Our Pentest Process
Fingerprinting: Gathering information from public sources about your organization and systems.
Automated Testing: Using tools to scan for known vulnerabilities in your WAN and/or LAN.
Manual Testing: Ethical hackers attempt to exploit vulnerabilities using various techniques.
Reporting: Providing a detailed report with findings, risk assessments, and remediation recommendations.
We can also assist with implementing solutions and conducting retests to ensure vulnerabilities have been addressed.
Why Choose BSM?
Over 15 years of experience in cybersecurity and penetration testing.
Certified and screened professionals with legal authorization (POB 1104) from the Dutch Ministry of Justice.
Personalized approach with direct communication between testers and your technical staff.
Flexible scheduling, often able to start within a few weeks.
Ready to Secure Your Systems?
Fill out our pentest form to get started. We’ll contact you promptly to discuss your needs and provide a no-obligation quote.
Request a Pentest
You can request a penetration test using our online form. We’ll contact you shortly after receiving it.
Which Pentest Fits Your Needs?
Discover the different types of pentests BSM offers.
Choose Your Pentest
Black Box Pentest
- Simulates an external attack without insider knowledge.
- Most realistic scenario.
Black Box Pentest
- No network diagrams or passwords provided
- Only IP addresses and URLs needed
- Most realistic scenario
- Sometimes mandatory (e.g. compliance or client demands)
Grey Box Pentest
- Balances realism and efficiency.
- Most commonly chosen option.
Grey box pentest
- Basic system information
- Server details and network diagrams
- Relevant IP addresses and URLs
White Box Pentest
White box pentest
- Include usernames and passwords
- Submit server details and network diagrams
- Share relevant IP addresses and URLs
- Internal testing: reveals all vulnerabilities
- Often combined with application testing

