The ICCM Audit
Why choose the ICCM Audit?
Developed by BSM based on 25 years of experience in cybercrime, the ICCM Audit is a fast and efficient internal security check that provides immediate insight into the security risks within your office environment. It identifies vulnerabilities in your information security and highlights areas for improvement across your entire organization — so you can take targeted action where it matters most.
The internal ICCM© Audit
At an average ICCM© Audit we usually find about 75 security holes!
ICCM Audit stands for:

What does the ICCM© Audit deliver?
Insight into your cyber resilience
Clear positioning on the cybersecurity maturity ladder
Identification of vulnerabilities in your IT security
Support with legal obligations, such as:
GDPR (Article 32): Obligation to implement appropriate technical and organizational security measures
Prevention of security incidents
NIS2 Directive: Mandatory cybersecurity and incident reporting measures in critical sectors
Prevention of managerial liability
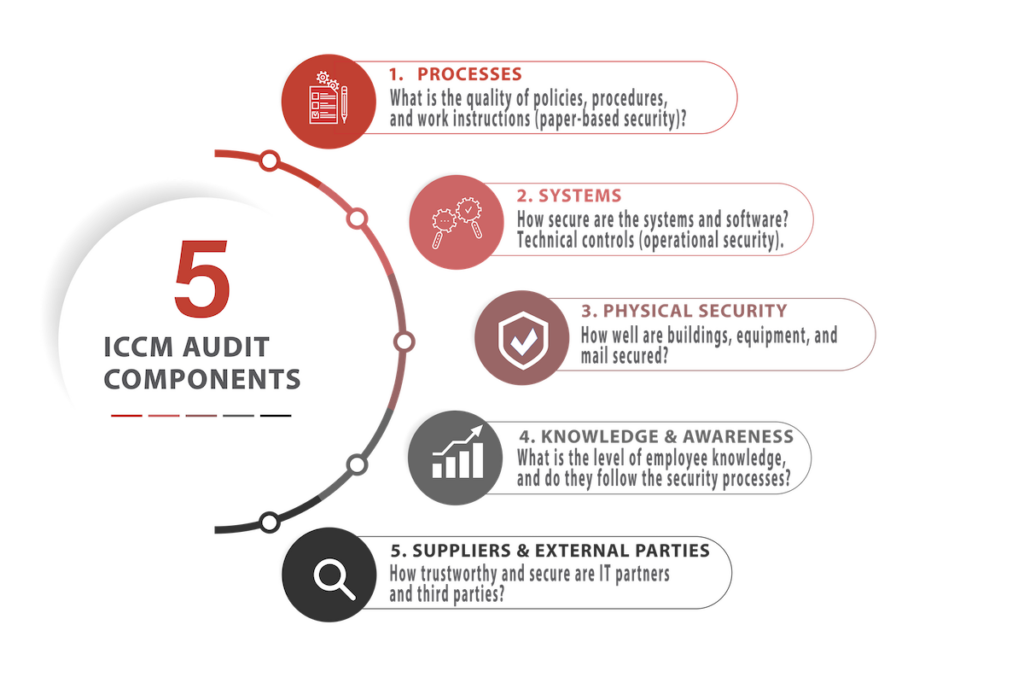
The ICCM© Audit analyzes your IT security based on five key aspects:
Process (“paper security”) – Which processes and work instructions are already in place? What is missing and where can efficiency be improved?
Systems – Our core competence: operational security. Random checks of the systems and software used by your organization.
Physical – Access security to buildings and mail, often the only aspect that is properly arranged.
Knowledge – What is the knowledge level of the employees? To what extent are processes understood, followed, and enforced?
Suppliers – Assessment of the quality and expertise of your (especially technological) suppliers.
Would you like to know more?
Request our brochure or schedule a consultation to discover how BSM can strengthen your organization’s cyber security. Contact us via email — we’ll be happy to provide you with the information you need.
Security Consultancy
BSM provides consultancy services on a secondment, interim or project basis.
Contact
Do you have questions about our possibilities or about what you need to optimize your digital environment in terms of security? BSM is happy to help you with any questions you may have.

